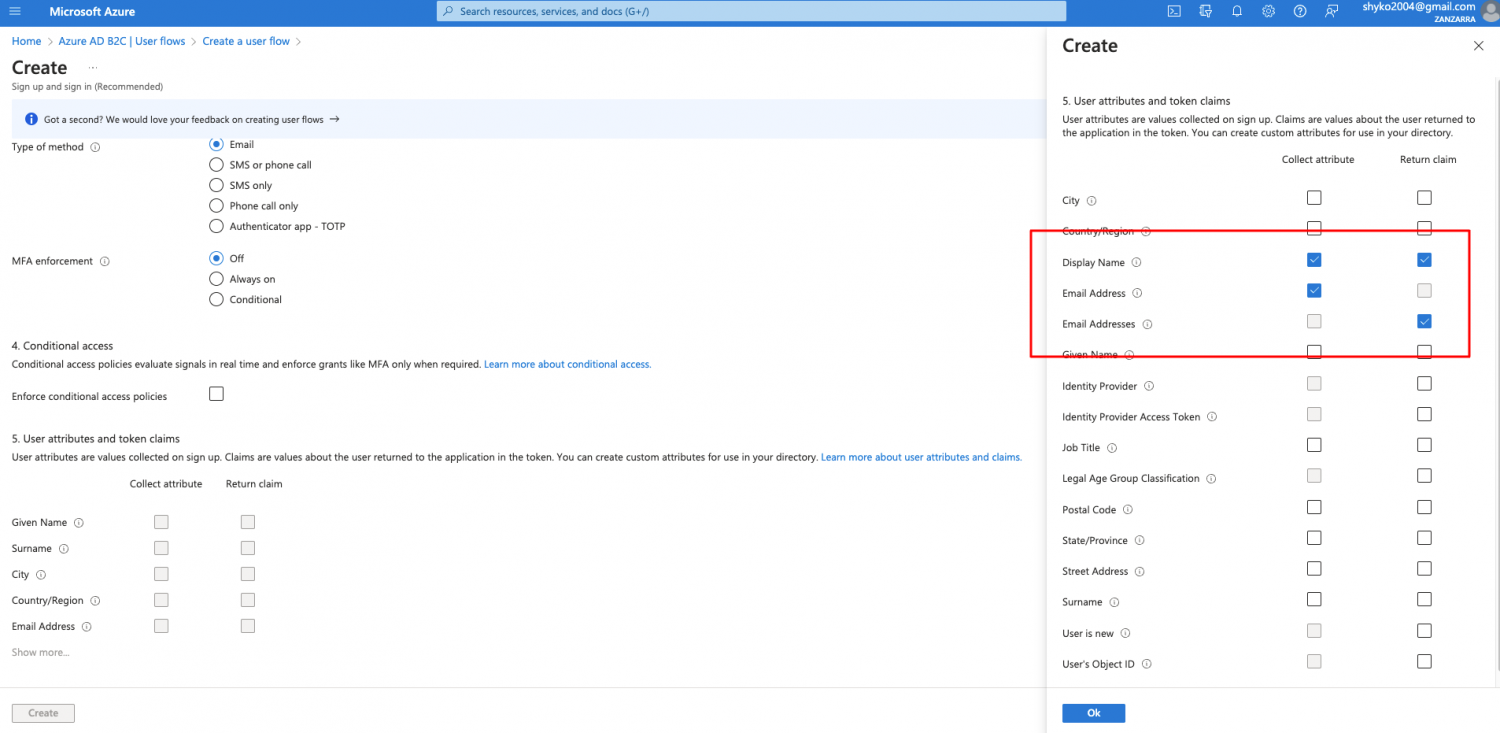
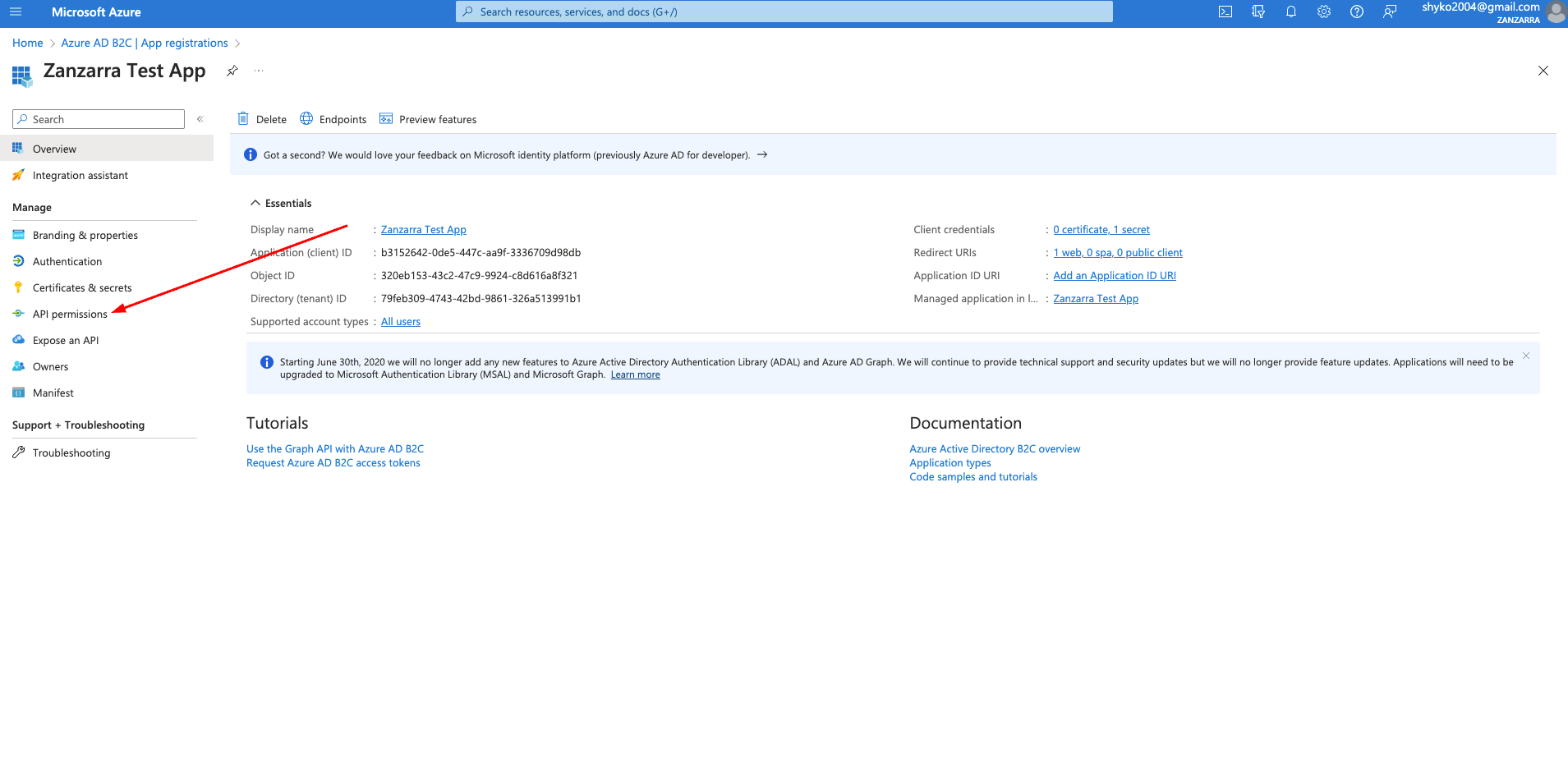
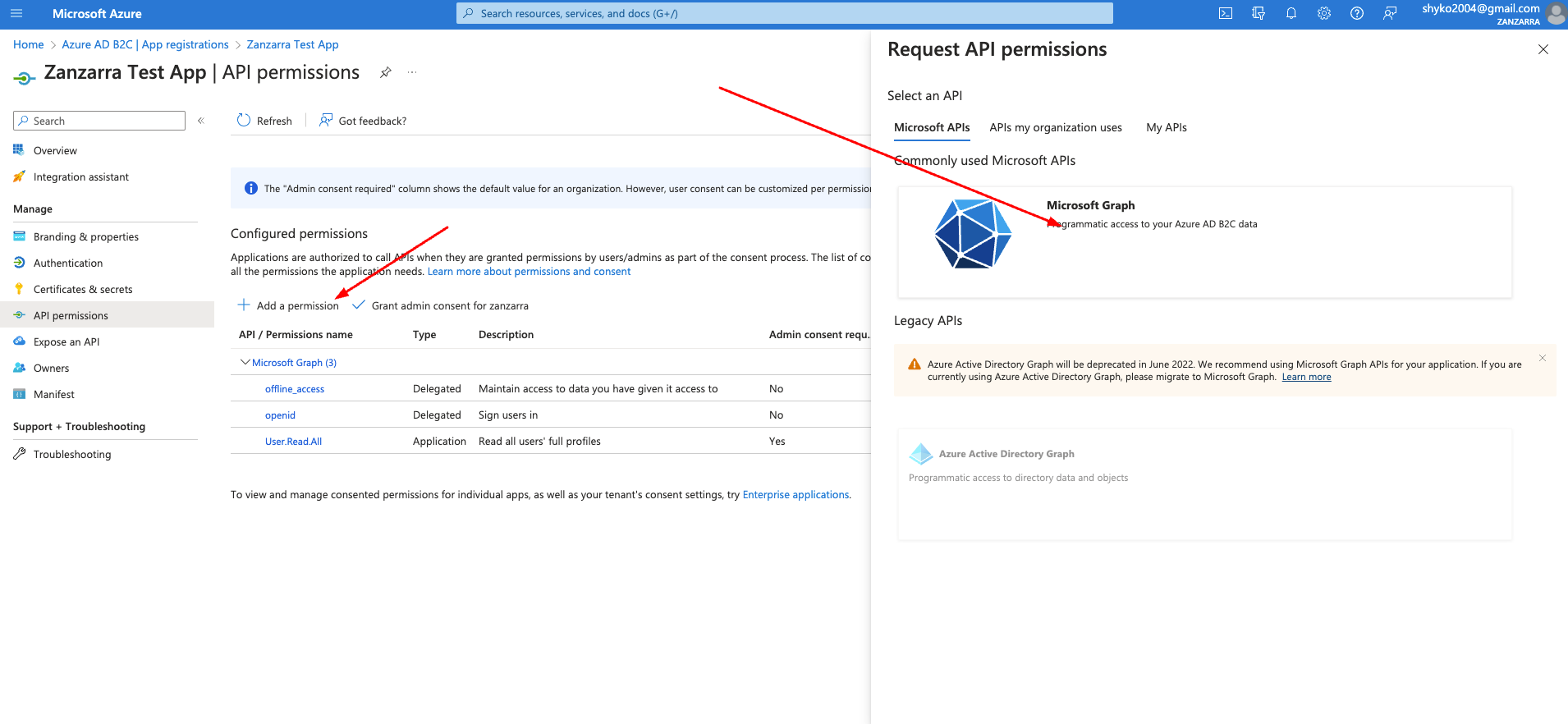
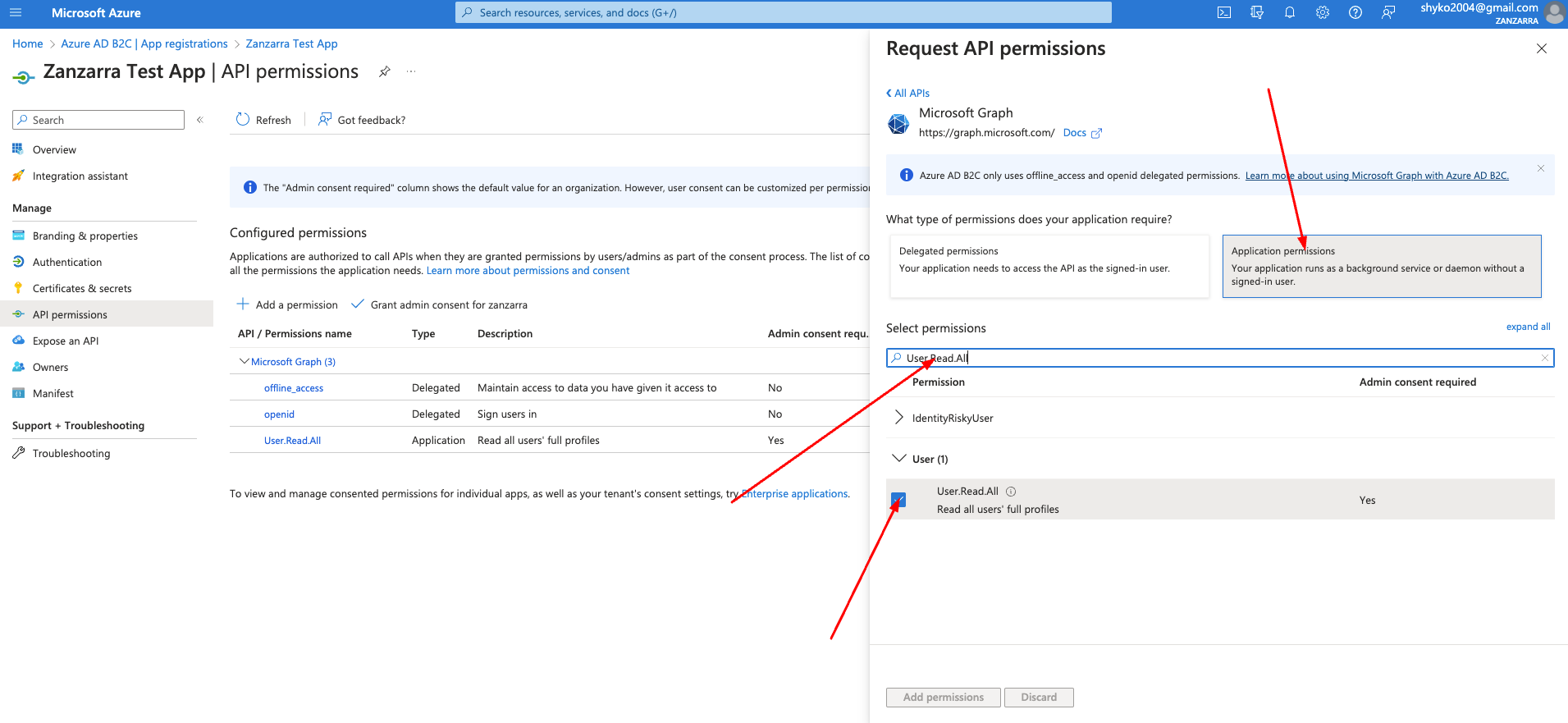
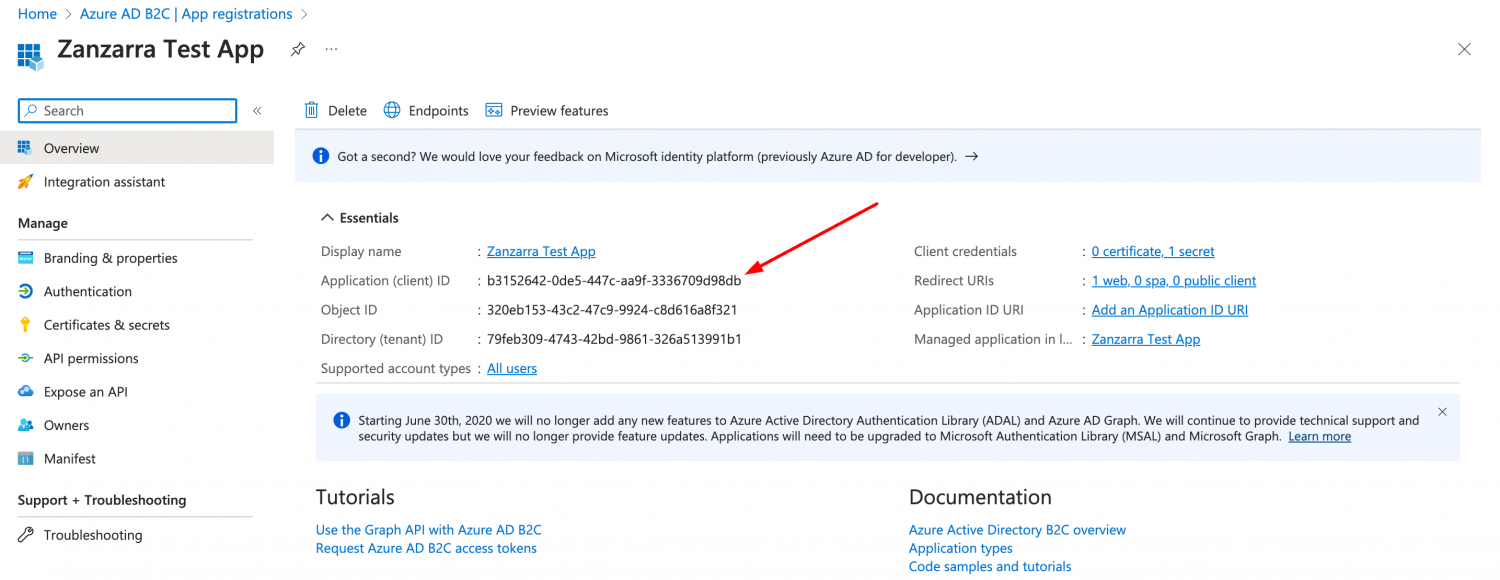
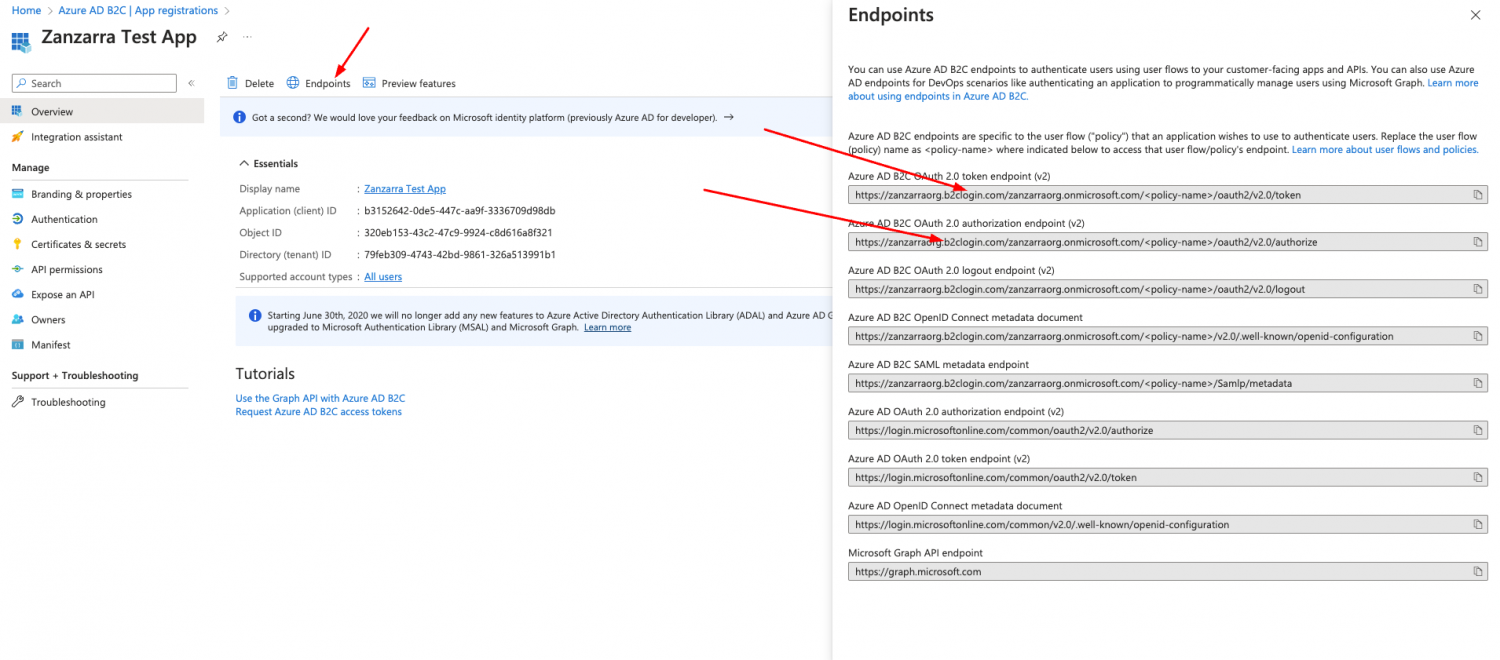
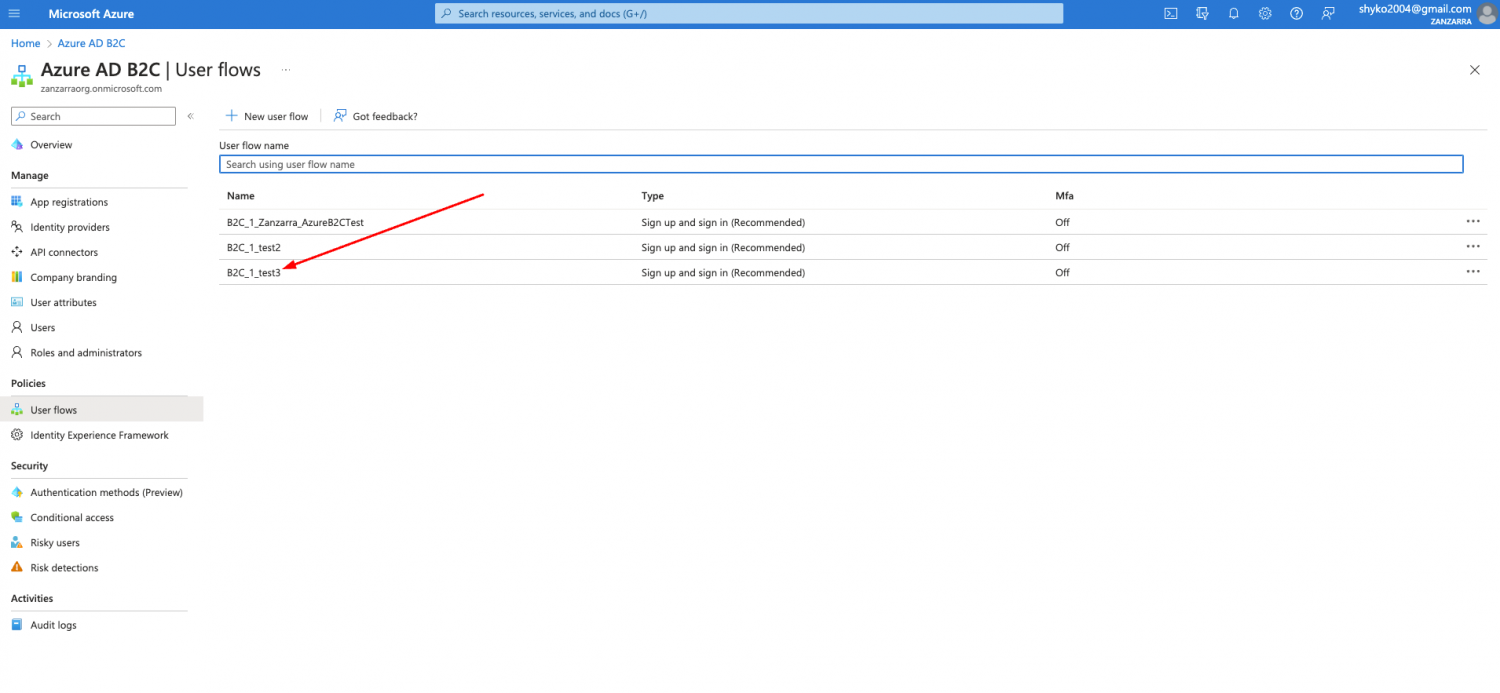
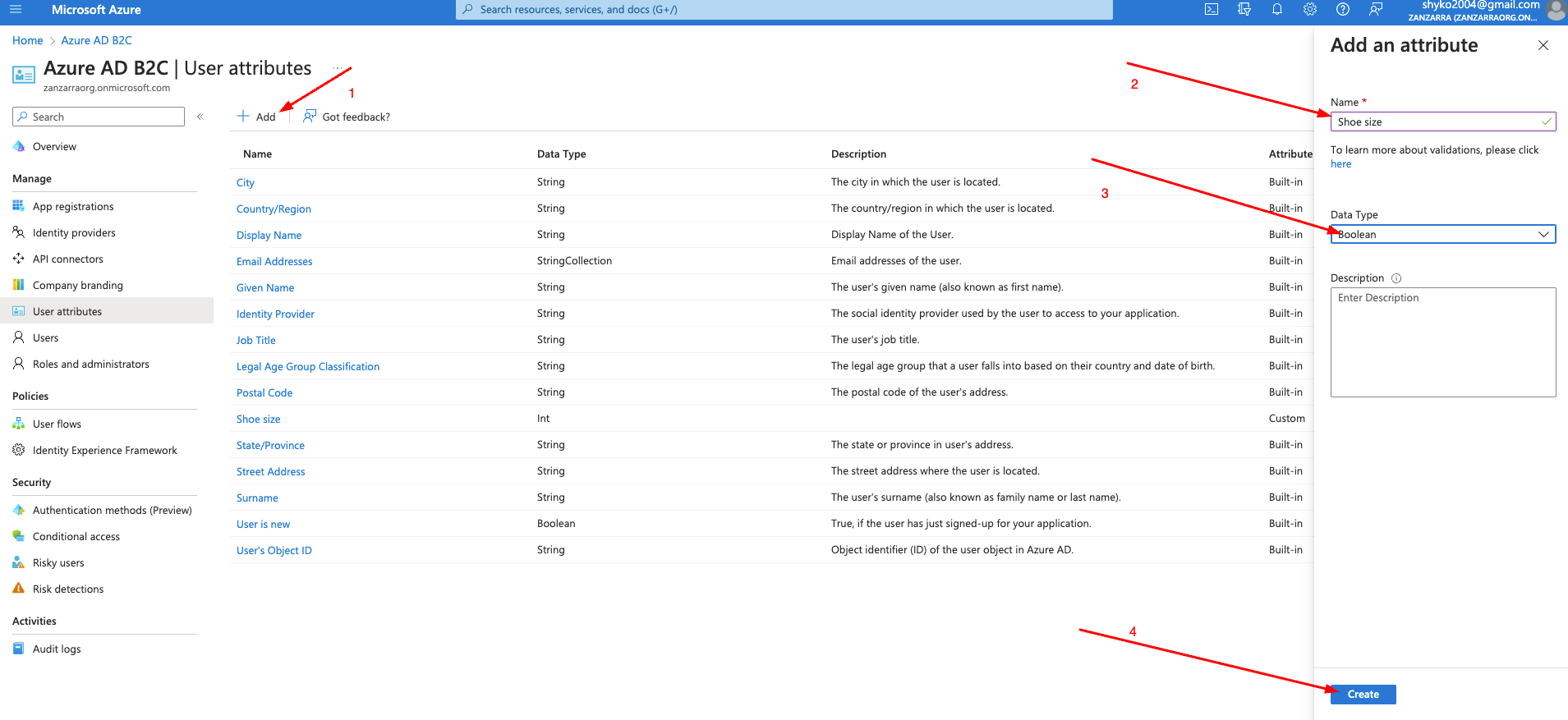
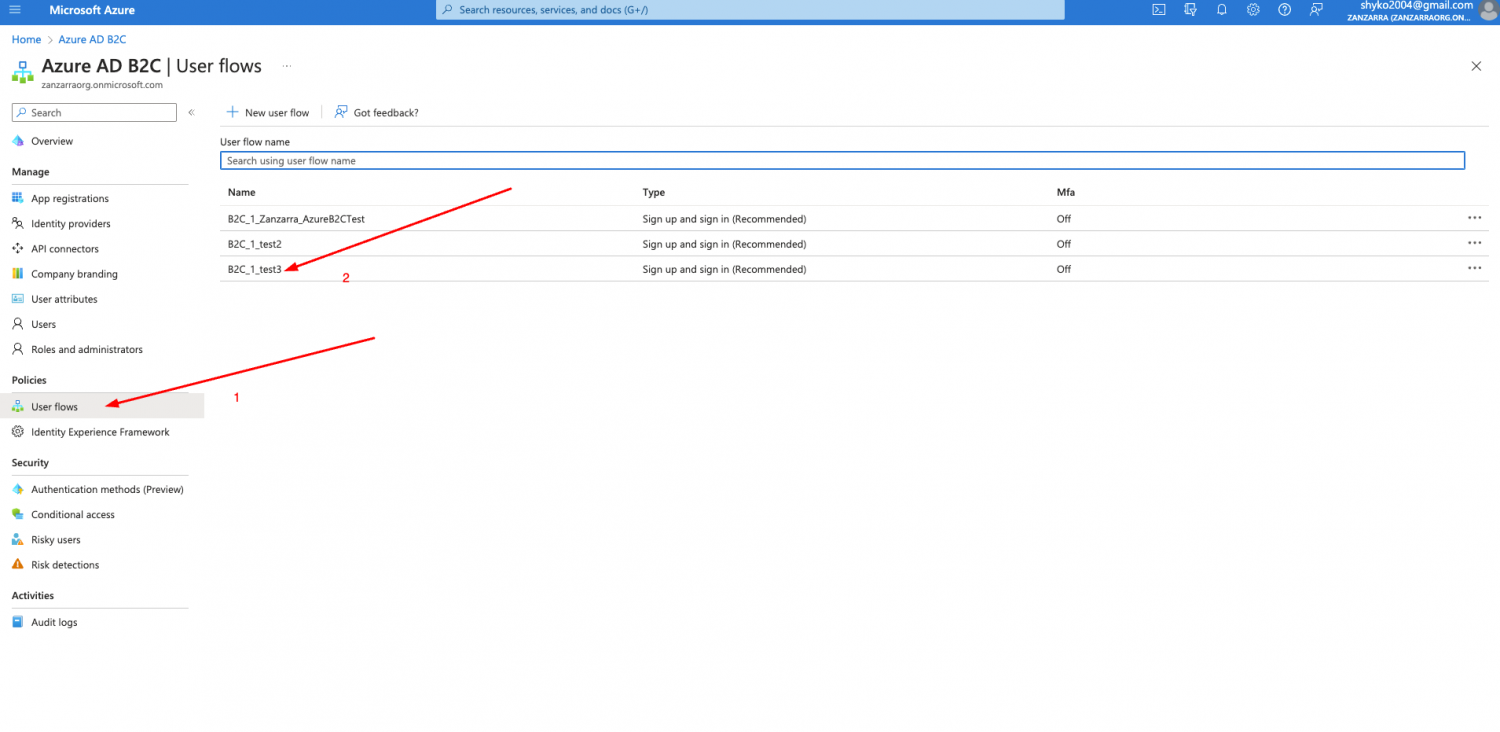
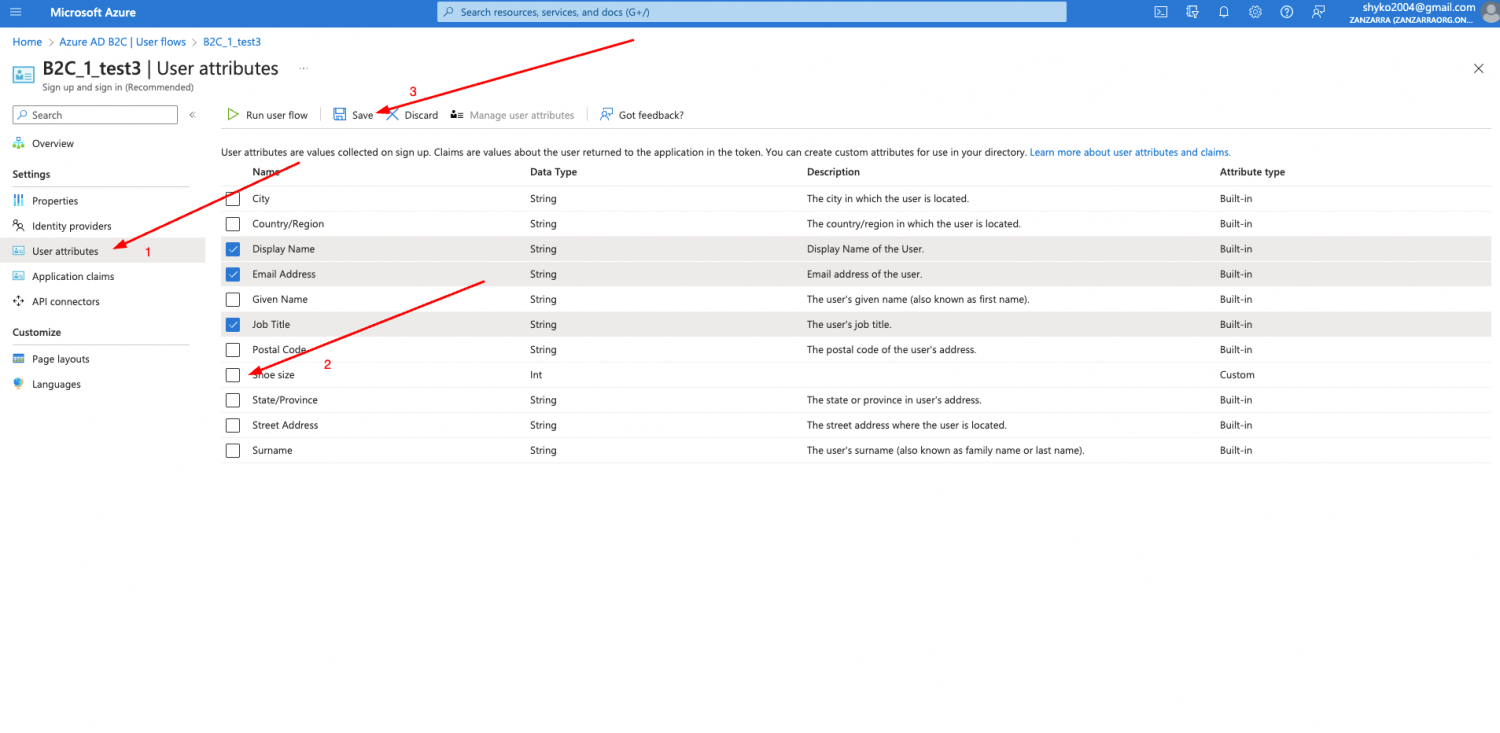
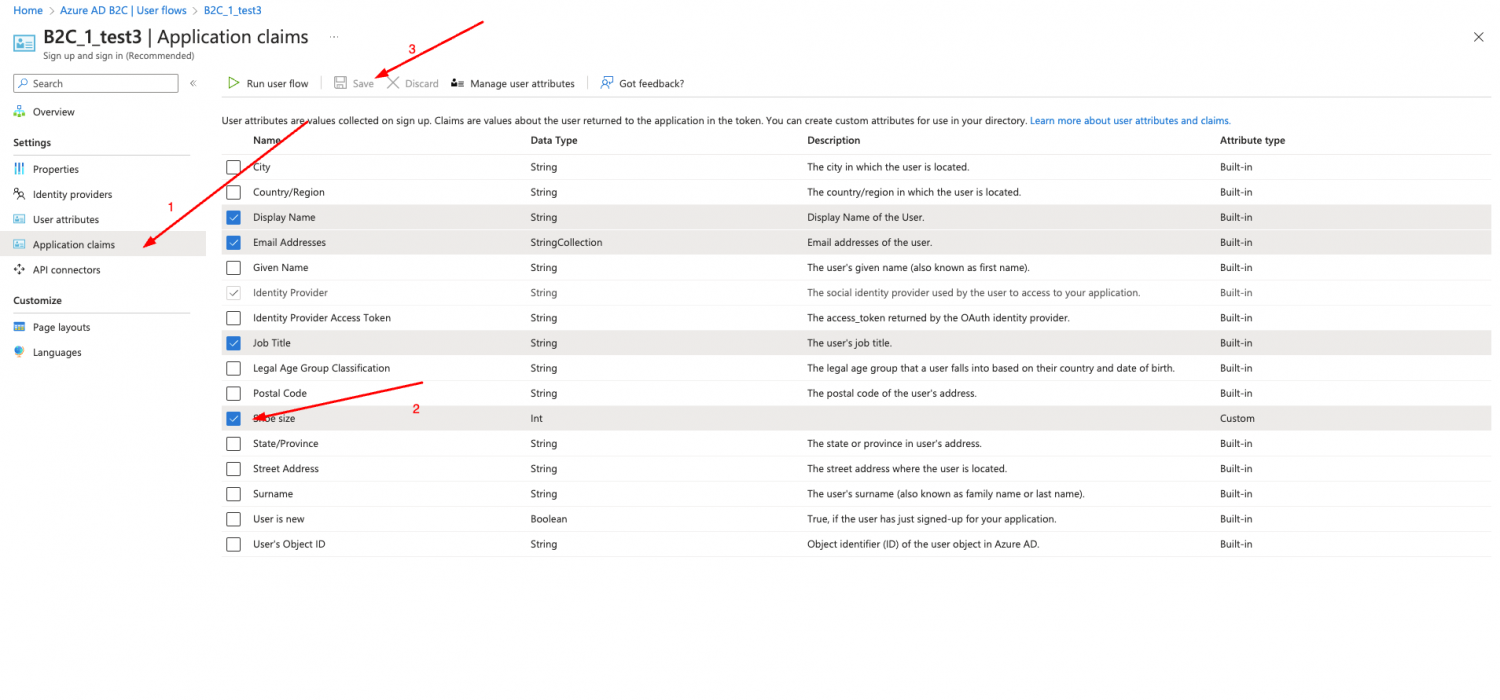
-
Prerequisites
You should login to Microsoft Azure with an account that is able to add or edit active directories.
Also, you have to create an Azure Active Directory B2C tenant. Manual
- create an Azure AD B2C tenant
- Link your tenant to your subscription
- Switch to the directory containing your Azure AD B2C tenant -
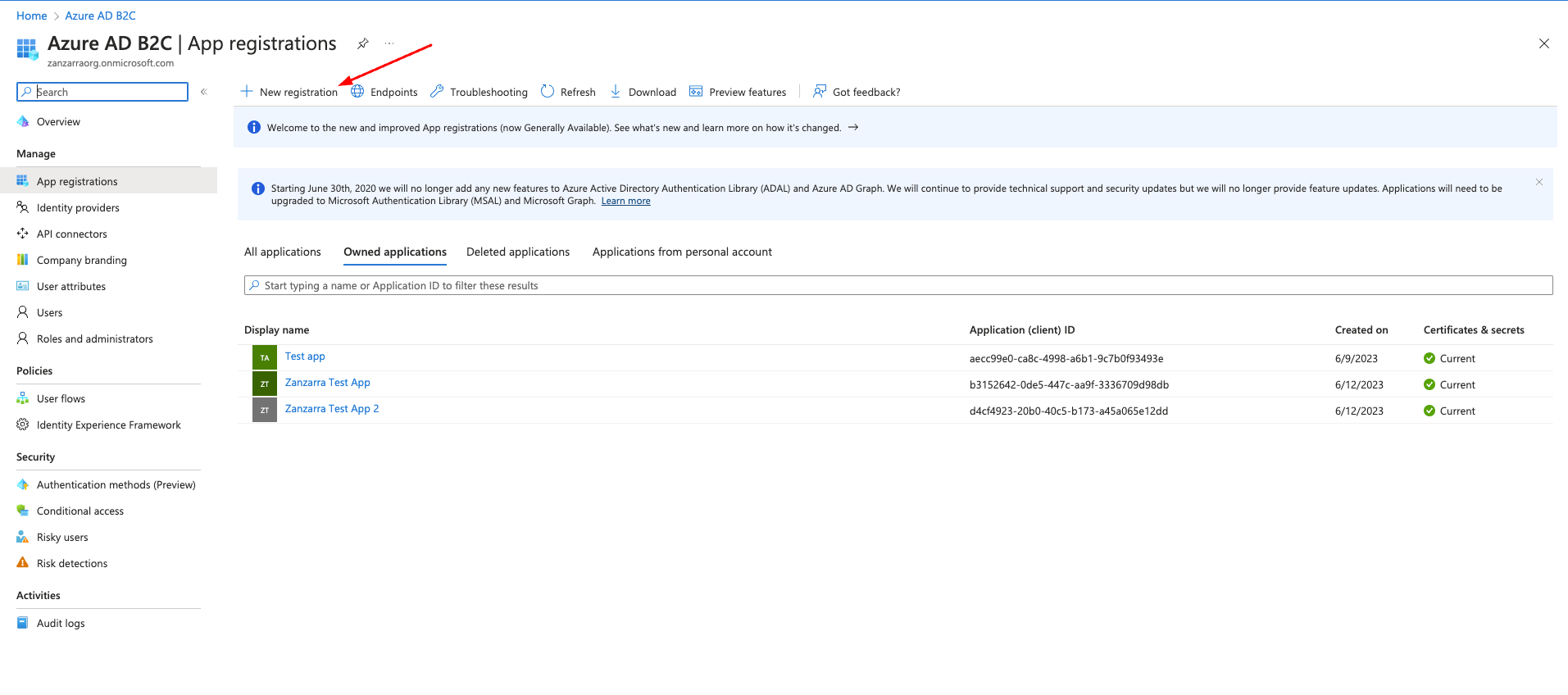
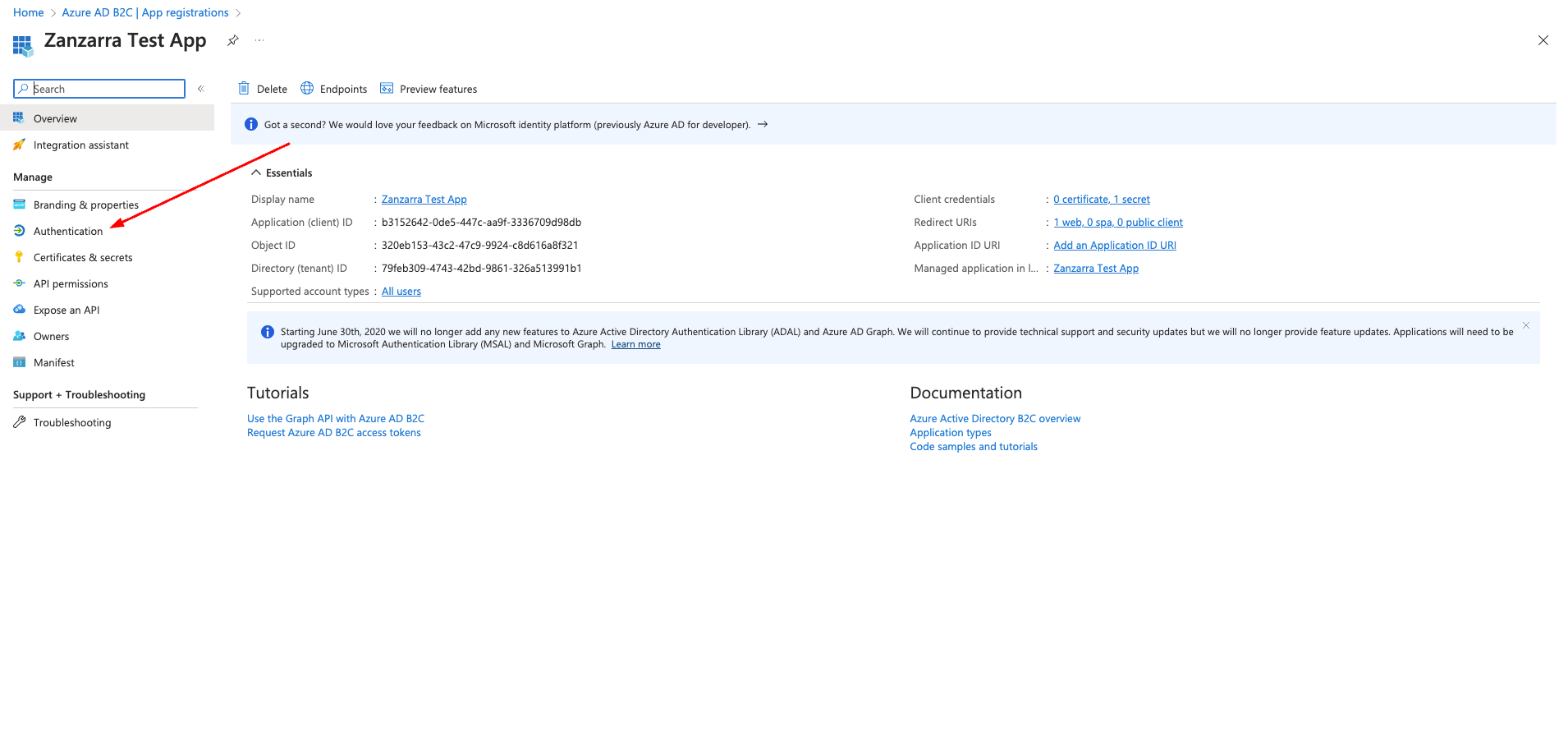
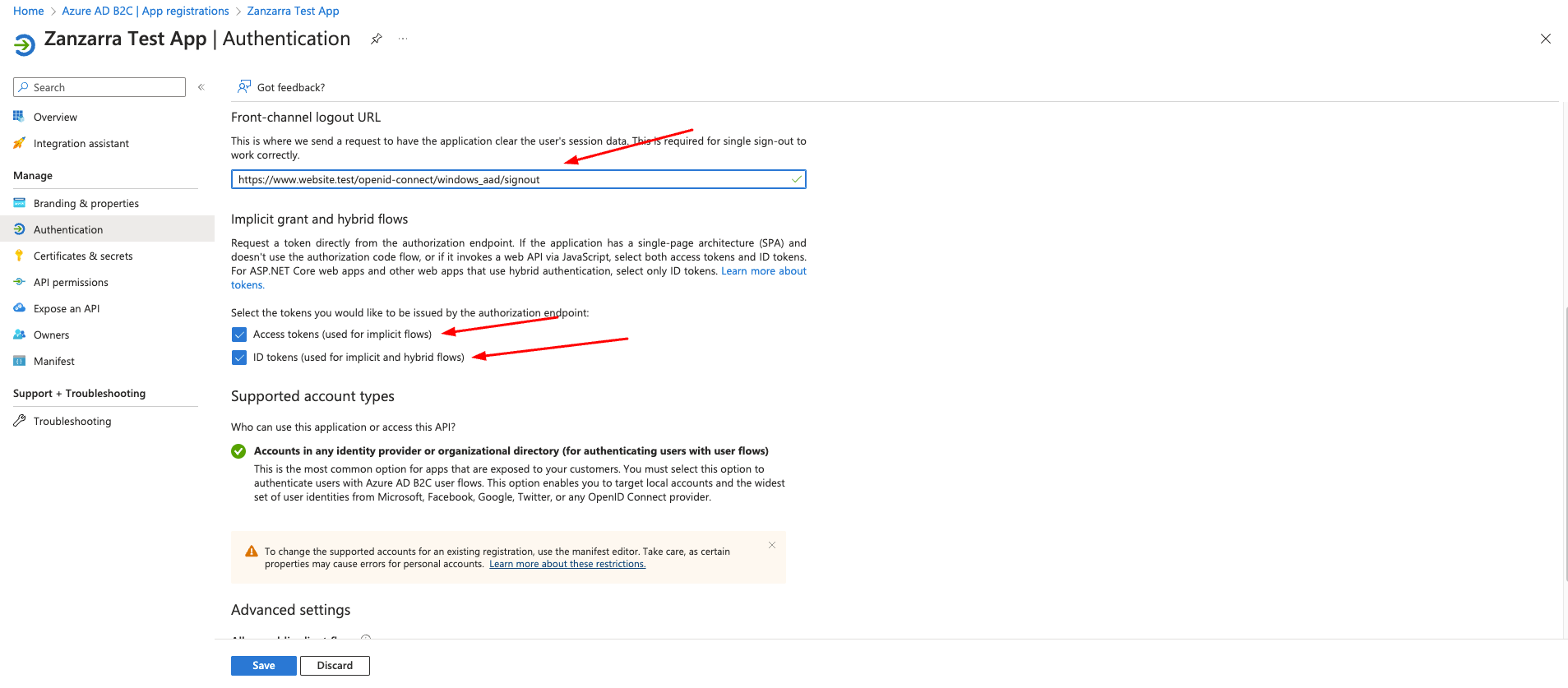
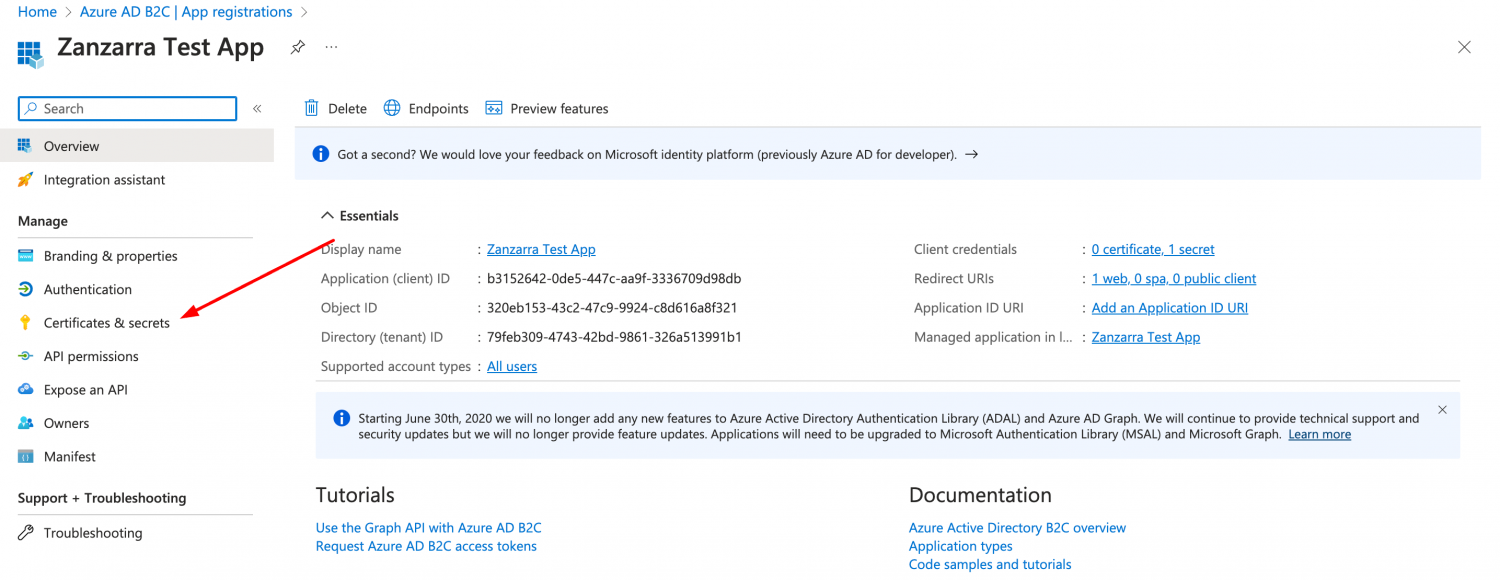
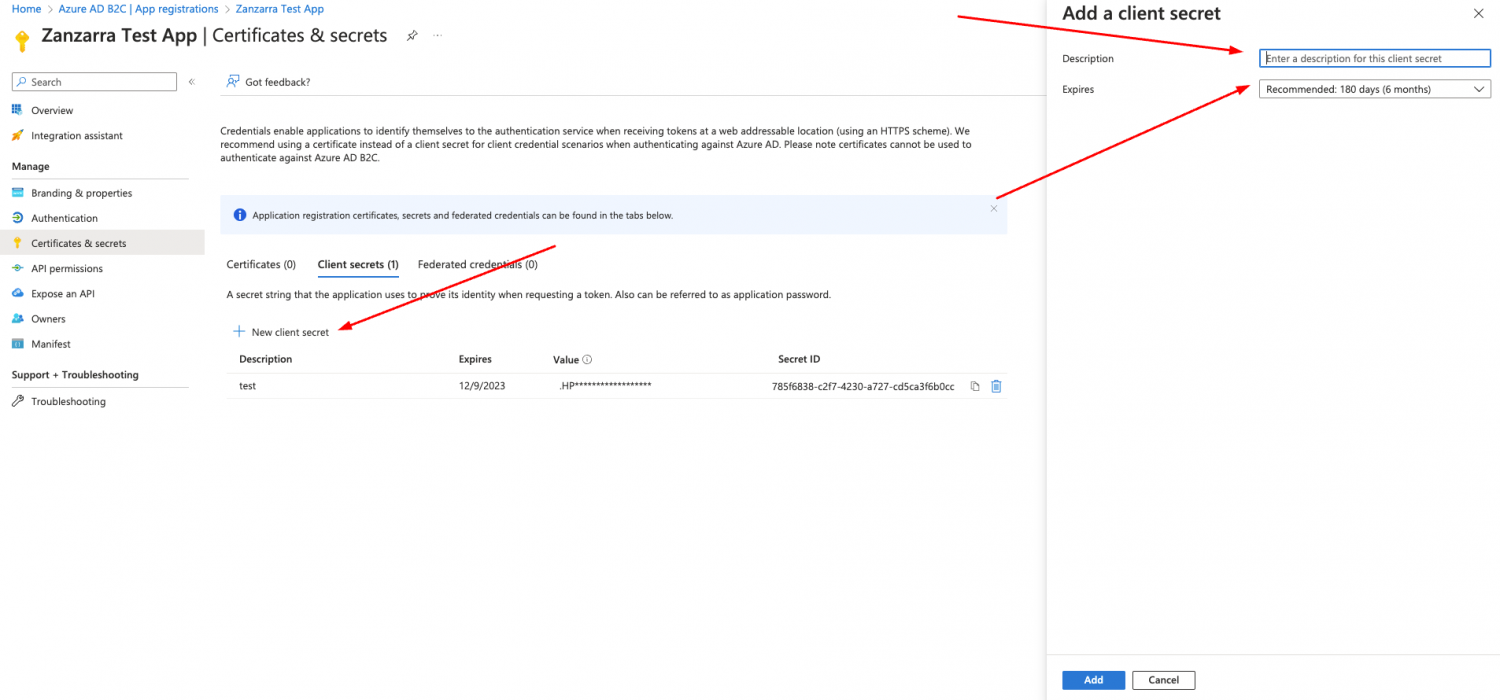
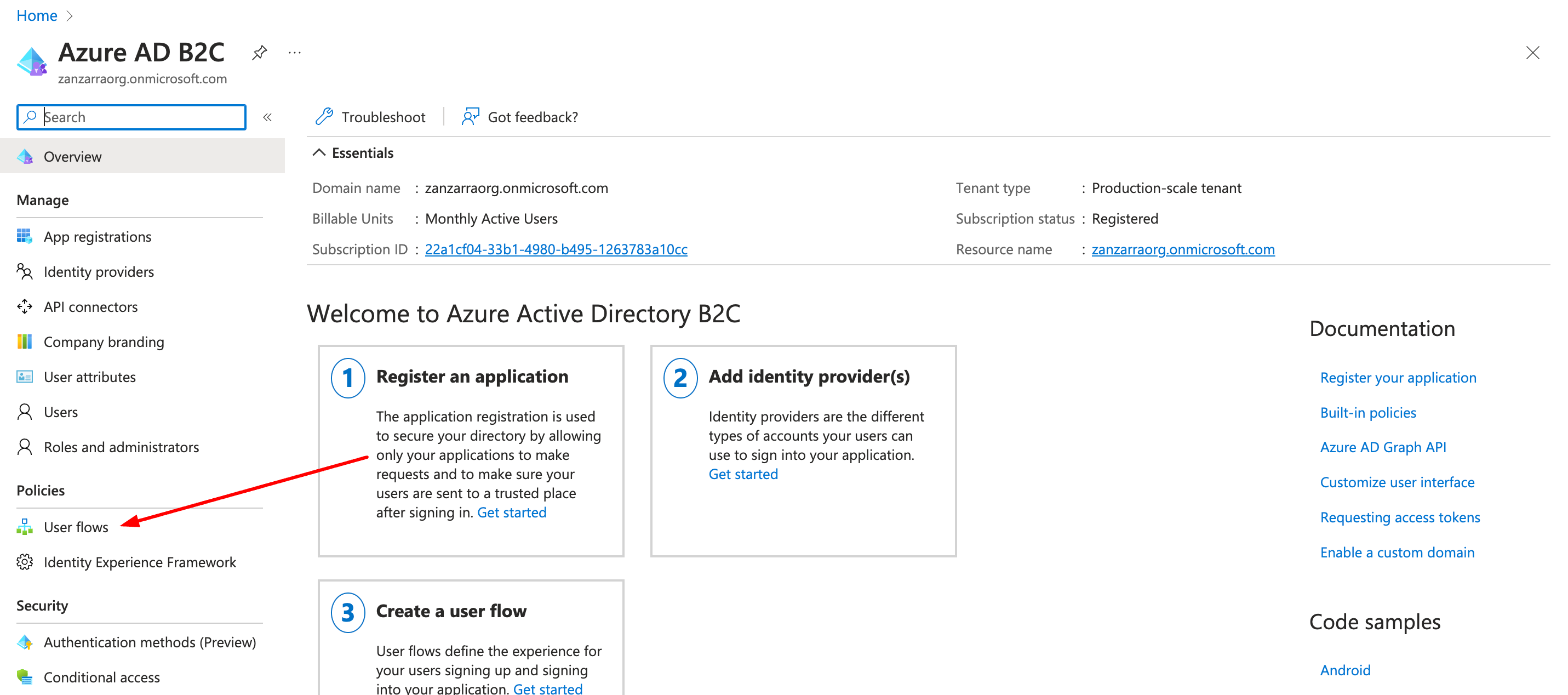
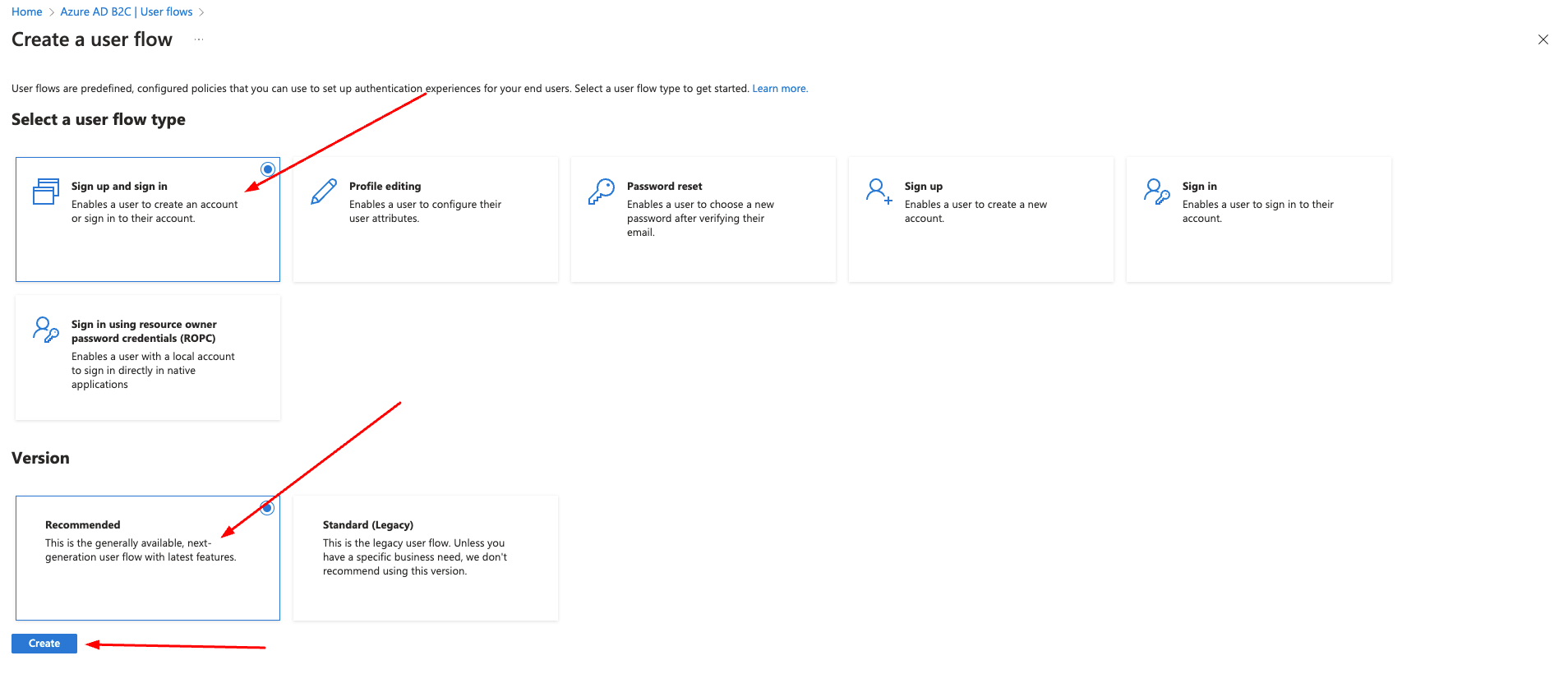
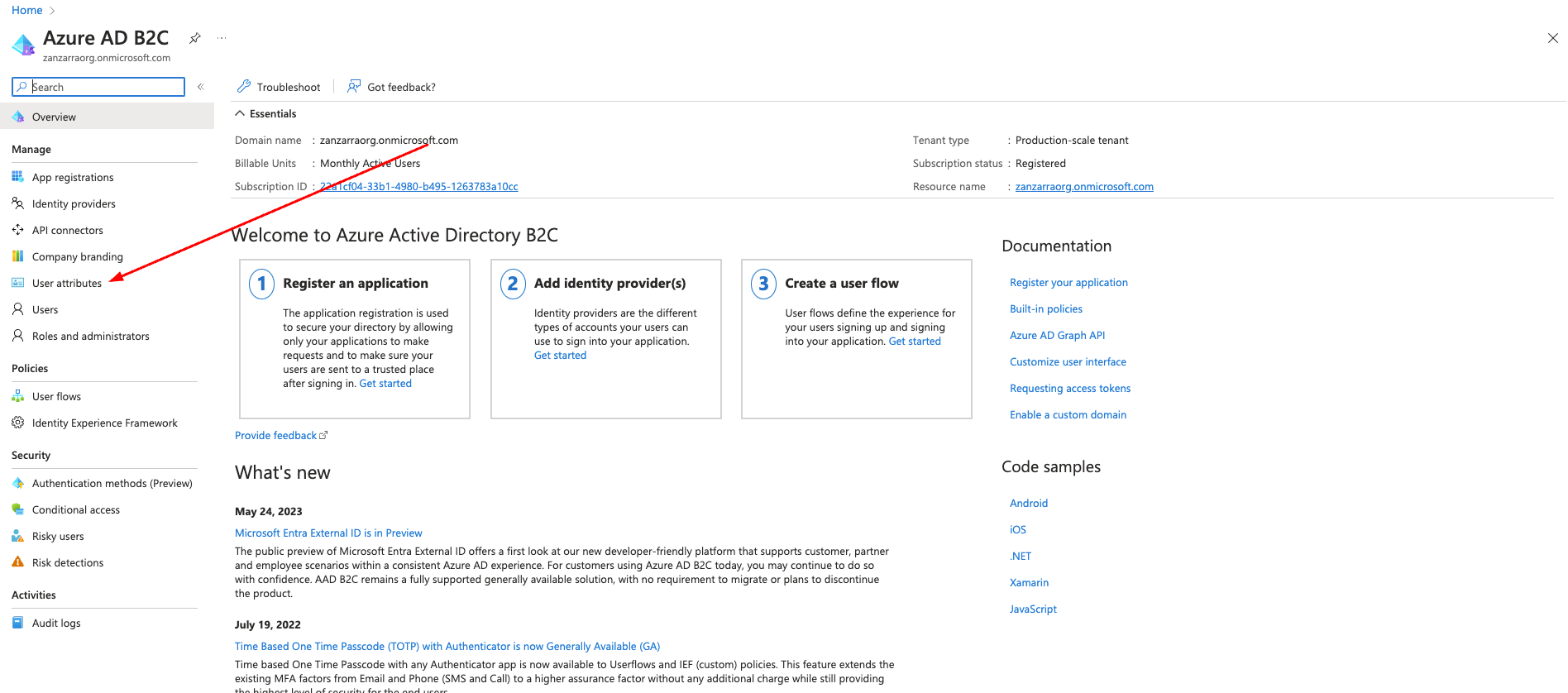
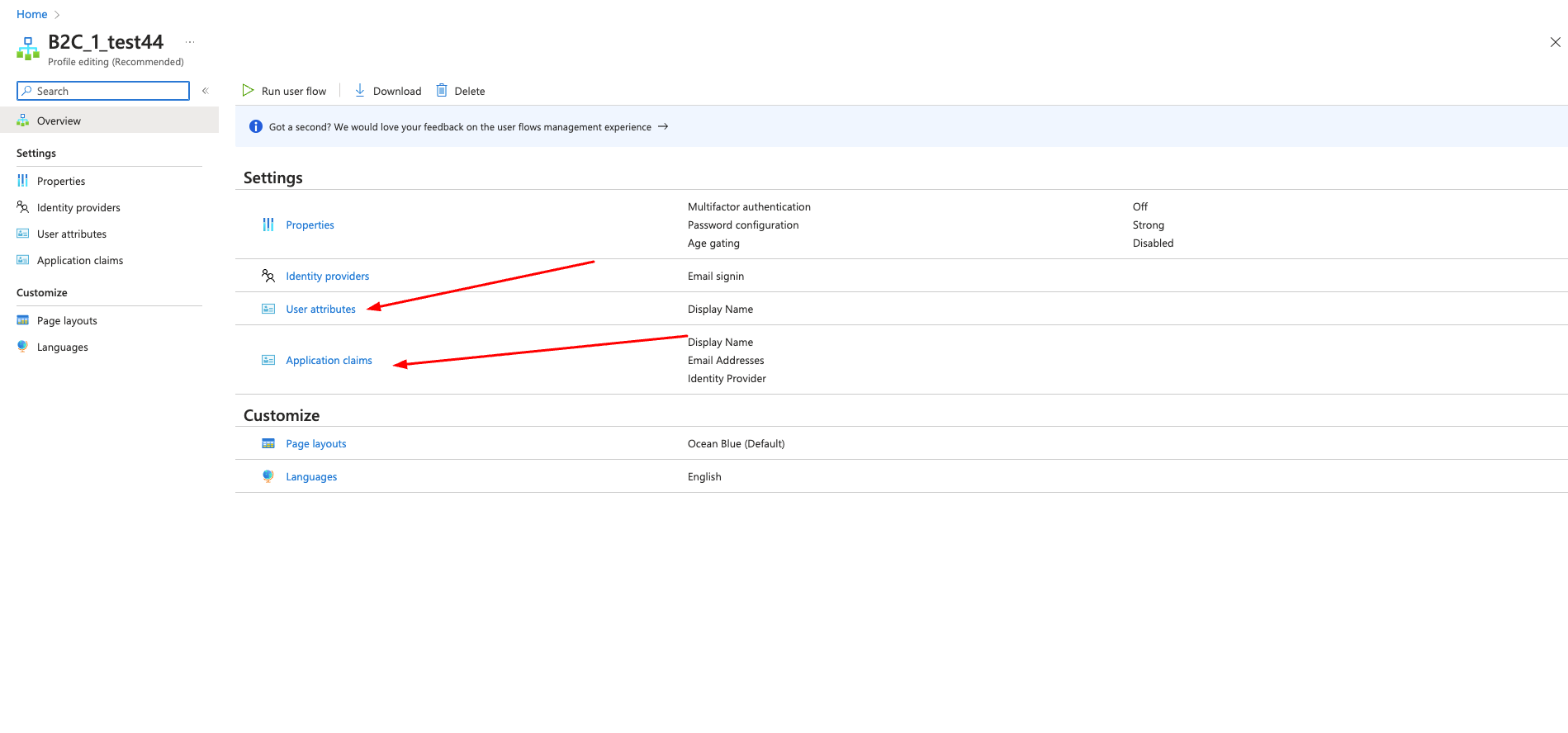
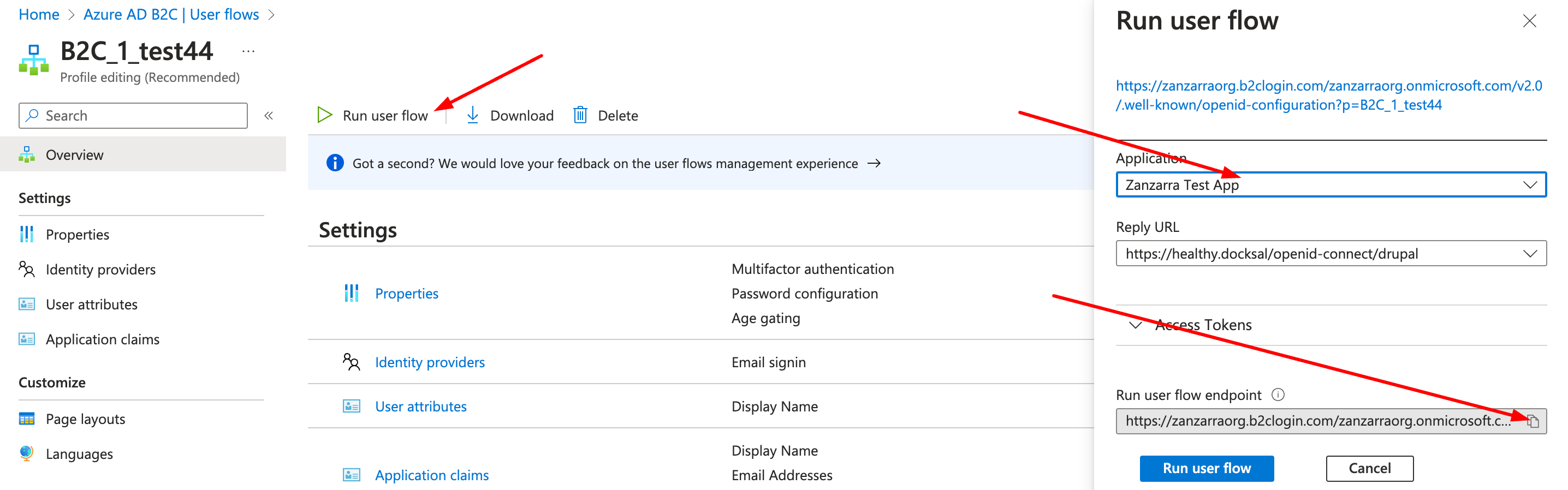
Steps in Azure
- Login to portal.azure.com
- Choose Azure AD B2C from the menu
When I've faced with Microsoft Azure documentation I was a bit frustrated. Seriously. It was like a giant maze with tons of text. And I spent a lot of hours while find the exit). So, let's go from words to deeds.